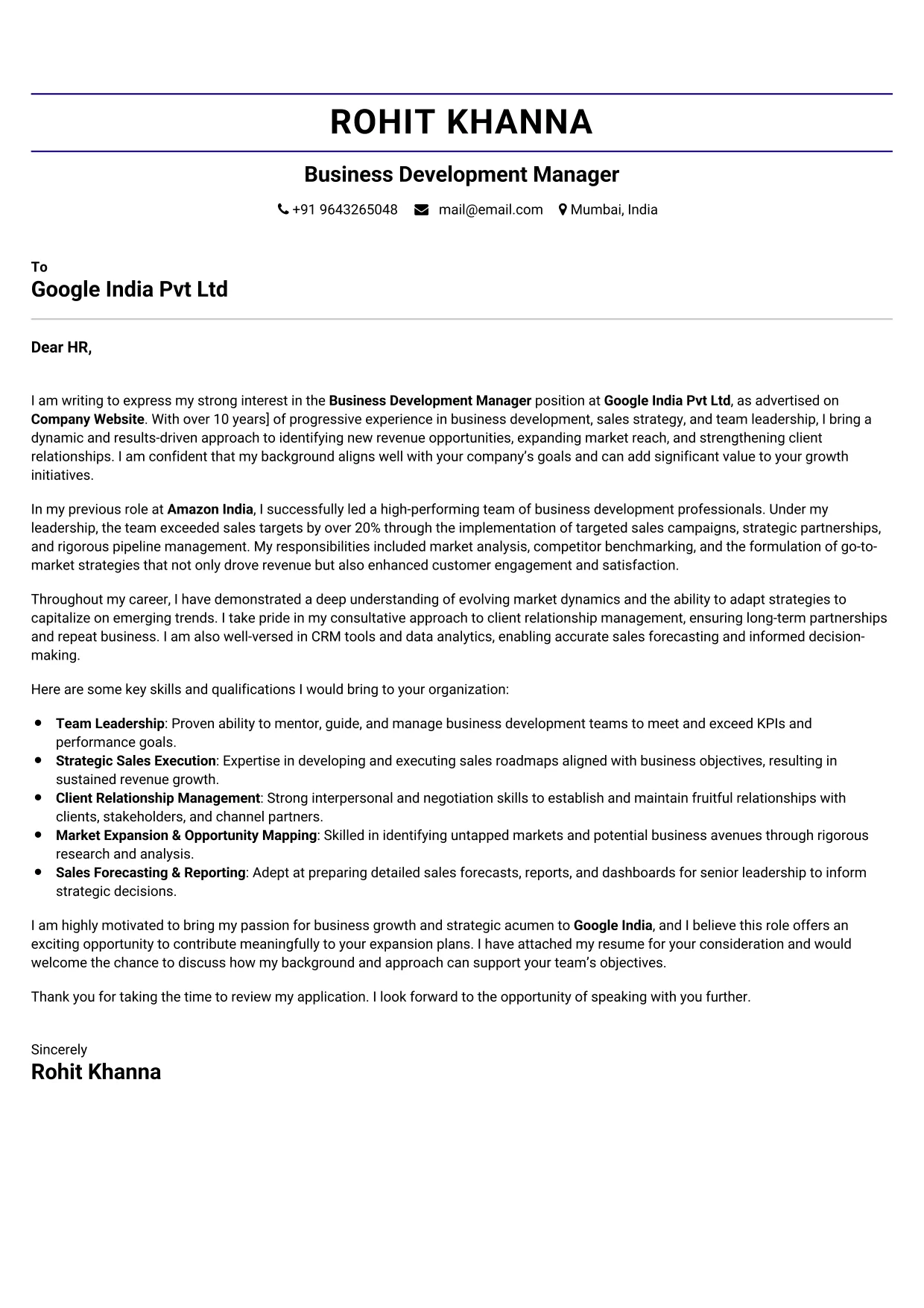
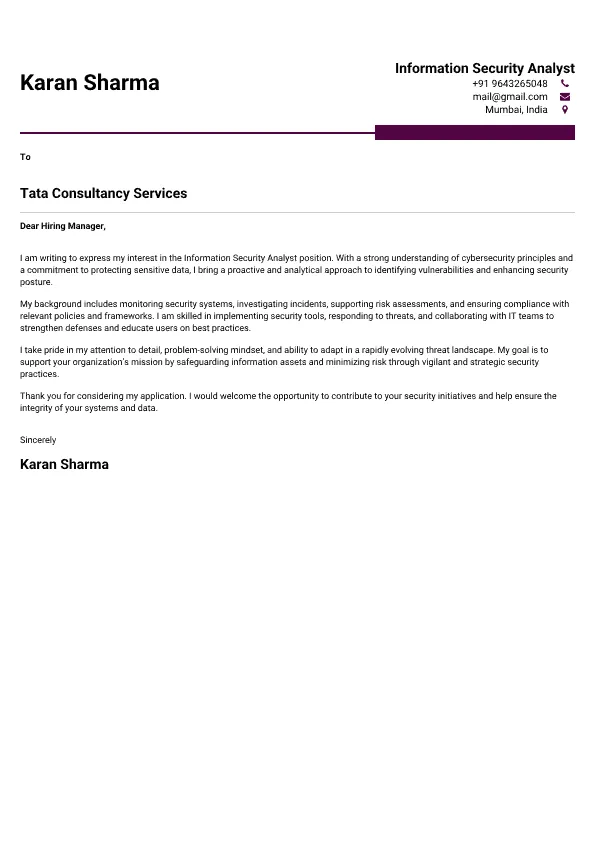
Information Security Analyst
Welcome to our Information Security Analyst cover letter sample page! This professionally designed template is crafted to highlight your expertise in protecting digital assets, identifying vulnerabilities, and responding to cyber threats. Whether you’re specializing in security operations, risk management, compliance, or incident response, this sample emphasizes key skills like SIEM platforms (Splunk, QRadar), vulnerability assessment, penetration testing (basic), incident response, network security, security policies, and regulatory compliance (GDPR, HIPAA). Tailored to meet 2025 employer expectations, this guide will help you create a compelling cover letter that stands out in the competitive cybersecurity field and secures your next vital role.
Superbresume.com empowers Information Security Analysts to craft cover letters that showcase their vigilance and technical acumen in cybersecurity. Our platform provides customizable templates tailored for demanding security roles, emphasizing expertise in threat detection, vulnerability management, and incident handling. With ATS-optimized formats, expert-written content suggestions, and real-time feedback, we ensure your cover letter aligns with complex security requirements. Highlight achievements like reducing successful cyberattacks, improving incident response times, strengthening security posture, or ensuring compliance with data protection regulations with confidence. Superbresume.com helps you create a polished, results-driven cover letter that grabs hiring managers’ attention and lands interviews for leading cybersecurity positions.
How to Write a Cover Letter for an Information Security Analyst
Address the Hiring Manager: Use the hiring manager’s name (e.g., “Dear Mr. Davies”) to personalize the letter and show attention to detail.
Highlight Relevant Experience: Focus on your experience with monitoring security events, conducting vulnerability scans, responding to security incidents, implementing security controls, performing risk assessments, or ensuring compliance with security policies and regulations.
Quantify Achievements: Use metrics prominently, e.g., “Reduced false positive alerts by 20% in SIEM system through rule optimization,” or “Decreased average incident response time by 15% through improved runbooks and automation.”
Incorporate Keywords: Include terms like “information security,” “cybersecurity,” “SIEM (Splunk, QRadar, Elastic Stack),” “vulnerability management,” “incident response,” “network security,” “firewalls,” “IDS/IPS,” “endpoint protection,” “risk assessment,” “compliance (GDPR, HIPAA, ISO 27001),” or “threat intelligence” from the job description to pass ATS filters.
Showcase Software & Tool Proficiency: Mention mastery of security tools, scripting languages (Python/PowerShell), and operating systems (Linux, Windows Server).
Emphasize Problem-Solving & Analytical Skills: Highlight your ability to analyze complex security logs, identify attack patterns, and develop effective mitigation strategies.
Demonstrate Communication & Collaboration: Include examples of effectively communicating security risks to technical and non-technical stakeholders, and collaborating during incident response.
Keep It Concise: Limit the cover letter to one page, focusing on your most impactful contributions to organizational security.
Close with Enthusiasm: End with a strong call to action, e.g., “I am eager to apply my information security expertise to safeguard [Company Name]'s digital assets and strengthen its cybersecurity posture.”
DevSecOps & Security Automation: Showcase expertise in integrating security into the CI/CD pipeline, automating security testing, and building security playbooks for rapid response.
Threat Hunting & Proactive Defense: Highlight experience in actively searching for unknown threats within networks and systems, beyond just reacting to alerts.
Zero Trust Architecture: Mention understanding and experience in implementing Zero Trust principles for enhanced access control and network segmentation.
Security Orchestration, Automation, and Response (SOAR): Familiarity with SOAR platforms for automating incident response workflows and improving security operations efficiency.
Behavioral Analytics for Insider Threat: Experience in using user and entity behavior analytics (UEBA) to detect anomalous activities indicative of insider threats.
Container Security (Docker, Kubernetes): Expertise in securing containerized applications and orchestrating platforms.
Supply Chain Security: Demonstrate understanding of risks within the software supply chain and experience in implementing controls to mitigate them.
Choose Superbresume.com to craft an Information Security Analyst cover letter that truly protects your career. Our platform offers tailored templates optimized for ATS, ensuring your expertise in threat detection, vulnerability management, and incident response shines. With expert guidance, pre-written content, and real-time feedback, we ensure your cover letter aligns with complex security requirements. Highlight achievements like reducing cyberattacks, improving response times, or strengthening security posture. Whether you’re focused on compliance or proactive defense, our tools make it easy to create a polished, results-driven cover letter. Trust Superbresume.com to showcase your indispensable skills and secure interviews for leading cybersecurity positions.
20 Key Skills for an Information Security Analyst Cover Letter
| Threat Detection & Monitoring | Vulnerability Assessment & Management |
| Incident Response & Handling | SIEM Platforms (Splunk, QRadar, ELK Stack) |
| Network Security (Firewalls, IDS/IPS) | Endpoint Protection & EDR |
| Risk Assessment & Management | Security Policy & Compliance (ISO 27001, GDPR, HIPAA) |
| Linux / Windows Server Administration | Scripting (Python, PowerShell) |
| Cloud Security (AWS/Azure/GCP) | Penetration Testing (Basic) |
| Authentication & Authorization (IAM) | Cryptography Basics |
| Problem-Solving (Cybersecurity) | Log Analysis |
| Communication (Technical & Non-Technical) | Attention to Detail |
| Threat Intelligence | Security Awareness Training |
10 Do’s for an Information Security Analyst Cover Letter
Lead with Security Impact
Highlight Key Security Domains
Quantify Achievements
Showcase Tool Proficiency
Discuss Threat Landscape Understanding
Optimize for ATS
Keep It Professional & Vigilant
Mention Compliance Knowledge
Proofread Meticulously
10 Don’ts for an Information Security Analyst Cover Letter
Don’t Be Vague About Incidents
Don’t Exceed One Page
Don’t Skip SIEM Experience
Don’t Use Complex Formats
Don’t Omit Communication Skills
Don’t Focus Only on Technical Vulnerabilities
Don’t Ignore Incident Response
Don’t Include Irrelevant Experience
Don’t Forget to Update
5 FAQs for an Information Security Analyst Cover Letter
Prioritize threat detection, vulnerability assessment, incident response, SIEM platforms (Splunk/QRadar), and regulatory compliance.
Use standard formatting, avoid graphics, and include keywords like “cyber defense,” “security operations center (SOC),” “risk mitigation,” and specific security tools from the job description.
Yes, absolutely. These certifications are highly valued and demonstrate foundational or advanced knowledge.
Describe a complex security incident or a persistent vulnerability you investigated, detailing your systematic approach to analysis, proposed solution, and the resulting improvement in security posture.
Use a professional, vigilant, analytical, and results-oriented tone, conveying your dedication to protecting information assets and maintaining a robust security posture.
Get 5x more interviews with our crafted Resumes. We make Cover Letter that land jobs.

Free Customized Cover Letter + Expert Resume Advice
Receive a professionally tailored cover letter absolutely free with every resume order—plus expert guidance to make your resume stand out.